PROTECT YOUR MONEY
Three Secret Anti-Hacking Tools that will Save you Thousands of Dollars and Hundreds of Hours in Downtime and Prevent Embarrassing Conversations with Vendors and Customers.
It’s a fact that every day many businesses lose hard-earned money at the hands of cybercriminals.
I’ve substantially strengthened defenses and reduced cybercrime-related losses in my business by implementing and enforcing strict employee Internet and email policies - and I can help you protect your business, too.
We have specific tools tailored for just these purposes and now we’re making those tools available to our customers. Without the use of these tools, it is almost impossible and difficult to keep cybercriminals from stealing your money.
These are powerful and must-use tools the cybercriminals don’t want you to be aware of and use because they protect your business, your life, and your money.
Cybercriminals have changed their methods by introducing the use of supercomputers to defeat your employees by exploiting human behavior and poor business practices.
It’s time to empower your employees with new and effective tools to keep them, your business and you protected.
Tools the Pros use to Protect Businesses and Fight Cybercrime
My name is Chris Adams, President of Adams Technology Group, Corp. and smadatek, our IT tech support, managed services and consulting division.
I’ve been doing this for over fifteen years and I understand how information is bought and sold on the dark web. Selling confidential information is a very lucrative cybercriminal business that continues to grow at an alarming pace.
Fortunately, my business already has a robust layer of cyber protection that many other businesses lack because of the unique tools available to us as IT professionals.
My staff and I also have ample expertise in identifying hacking schemes and neutralizing threats because we see them every hour of every single day.
These threats are becoming more stealthy and are difficult for the average employee and business owner to recognize.
You need to protect your business like I protect mine and many others.
My tech group uses defensive tools against cybercrime that aren’t even on the radar of many other businesses. Our strongest line of defense is software that helps us create and manage our usernames and passwords to prevent hackers from finding routes into our software.
These tools were developed for this specific purpose. We manage thousands of usernames and passwords on a daily basis- our own and those of our customers.
You use a multitude of usernames and passwords and without adequate controls in place, your business will continue to be an open invitation for hackers.
In this article, I’m going to correct misinformation about cybercrime and reduce your confusion to help stop criminals from stealing your money.
I’m also going to share valuable information and provide some tools you can use to protect your important and proprietary data and keep your money safe.
We have to fight these criminals together!
There’s no worse feeling than having something stolen from you, or realizing that you unknowingly allowed something to be stolen from someone else- like the boss.
That pit in the bottom of your stomach- the one that grows as you try to assess the damage and rush to isolate the issue and minimize the damage? You can prevent it from ever happening.
In order to stop thieves from attacking our businesses, we must collectively become more proactive about securing our networks. We must go on the offense.
Hardware, firewalls and other software have a partial role in keeping businesses safe but they’ve also created a false sense of security.
Firewalls, VPNs and antivirus software create a false sense of cyber protection
Executives, owners and employees need to stop believing they are protected by firewalls and other pieces of software running in the background on their PCs or laptops.
This false sense of security sets them up for attack from outside forces in several ways:
It encourages them to be careless and even cavalier when it comes to creating usernames and passwords.
It reduces concern when choosing the websites they visit.
It discourages thoughtful consideration of whether emails are safe, resulting in opening potentially dangerous emails and attachments.
There’s little attention given to sharing information via your network, either purposely or simply by accident.
The two pieces of information every cybercriminal is after are a username and password.
And, as we continue to move more of our business applications into the cloud, we’re required to create, share and manage even more credentials, making our personal and professional lives more vulnerable to cybercriminals.
Cybercriminals prey on human error and predictable behavior
We must prevent password creation and management from falling victim to simple human error and behavior.
FACT: the greater the number of passwords we must keep in our memory, the more likely we are to reuse them or make them easier to hack.
We also lose track of them when frequently prompted to create new ones, often by automated password reset rules or time-lapse policies, like the annoying one from the bank that requires a change every thirty days.
FACT: this practice is misguided and ineffective
Requiring password changes every thirty days produces counterintuitive results.
Although the practice of frequent changes is intended to improve security, in reality it leads to shorter, easier to remember passwords that are also easier to guess and to hack.
The reason is obvious: But realistically, people choose simpler passwords that are easy to remember, because the lifetime of the password is short. Very few people create complex passwords when they’ll last just 30 days.
As humans, we typically create passwords that are easy to remember.
Cyber criminals rely on us taking the easy way out with passwords we can remember — and passwords they can easily uncover.
The simplicity we seek in creating memorable passwords is exactly the predictive behavior that subjects us to being hacked.
Businesses and individuals need to engage in strong password practices that include the following:
12 character passwords are obsolete.
25 character passphrases are required.
Each user must have a unique username and passphrase for each website that requires a username and password.
Passwords are never shared with another person- not even a trusted co-worker.
Usernames, passwords, and similar login credentials are NOT saved in internet browsers such as Chrome, Firefox, Safari, Opera, or Microsoft Edge.
Employees are not permitted to use personal email for business logins.
Conversely, employees are not permitted to use business email for personal logins.
According to research by the National Institute of Standards and Technology (NIST), our customary password habits are dangerous and make businesses and individuals vulnerable to cybercrime.
Passwords and human behavior create a weak link
How many of us have added a number “1” or a “!” to the end of a password? Cybercriminals know about this very predictable pattern.
In other troubling news, using password hints is also dangerous. Diego Poza, in his “Best Practices for 2020” blog, states, “With the constant dissemination of personal information on social media or through social engineering, the answers to these prompts are easy to find, making it easy for attackers to breach your user’s accounts.”
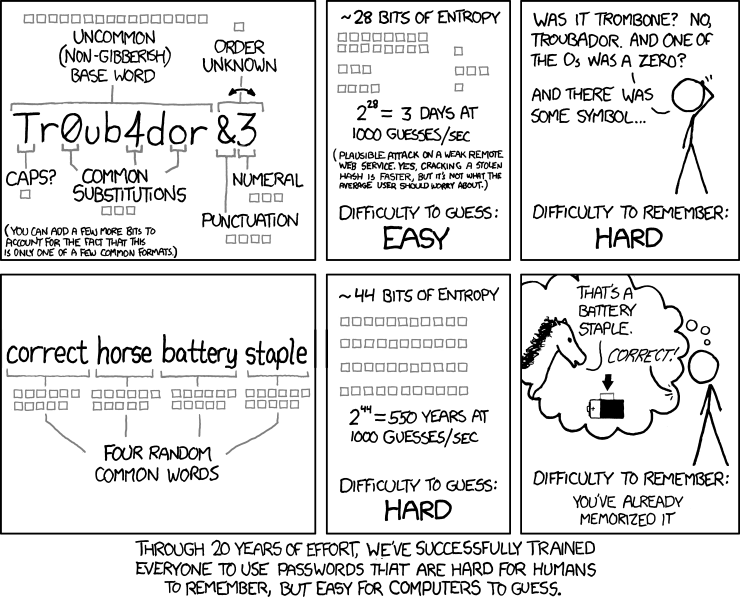
“Through 20 years of effort, we’ve successfully trained everyone to use passwords that are hard for humans to remember, but easy for a computer to guess.”
Here are some tools the pros use to protect themselves and their customers:
Pro Tool #1: Use a messaging tool to enhance inter-office communication among employees. It’s a fabulous way to reduce interoffice email noise and keeps inboxes clutter-free. Think of it as another form of email verification or a way to reach out for instant clarification.
Pro Tool #2: Use a breached password detection tool that protects and notifies users when their credentials are leaked to a third party. You can optionally prevent access until the user has reset their password. This tool is invaluable when it comes to password integrity.
Pro Tool #3: Use a password-generating tool to create strong, random passwords. This will allow the creation of random passwords for every site that requires them and removes the vulnerability created by someone using the same password repeatedly.
Here are some bonus pro tips to provide cybersecurity to protect your money:
Pro Tip #1: Restrict employees to only ONE Internet browser. Make sure the chosen browser has the correct settings to facilitate the above tips. Additionally, prohibit the downloading of any other browser so employees don’t circumvent the measures you’ll be using to enforce the password policy.
Pro Tip #2: To create a super-strong passphrase take a short phrase, like the lyric to your favorite song or a memorable quote, and:
- Capitalize a random letter.
- Replace a letter with a number such as replacing the letter “E” with the number “3.”
- Add an underscore or dash between words.
A great master password is a passphrase utilizing four common words. As the picture depicts, a strong password using the passphrase methodology would take more than five hundred years to crack.
Some examples include:
Nascar_camping_work_Maui
Baking_sk11ng_sleep_dr!nk
or a song lyric like
Ro11_0ut_tHe_b@rre!
Passwords are more valuable than a social security number!
Passwords are the common denominator for every cybercriminal plotting to steal your money.
A password is the single most important piece of information you possess, and its value demands careful protection and management.
When businesses don’t implement rigorous password policies, cybercriminals continue to steal important information and sell it to other criminals on the dark web.
In order to protect your assets and prevent cybercriminals from stealing your money and jeopardizing your livelihood, password protection is the highest priority for preventing disaster.
Conversations your Business Wants to Avoid:
Your business doesn’t want to:
Let your vendors know you’ve been hacked.
Tell your customers their information has been stolen.
Task employees with explaining unauthorized financial transactions.
Resort to filing police reports because you failed to protect your assets from cybercriminals.
These conversations, and the security breaches that necessitate them, are both humiliating and costly in terms of cash.
Additionally, security breaches destroy your company’s reputation with current clients and can jeopardize your reputation with future clients, who will question your capacity to serve them safely and effectively.
If cybercriminals raid your proprietary information, in addition to the money they’ve stolen, you’ll lose even more money to have the threat identified and neutralized. That’s a “lose/lose/lose” for you, your business, and your customers.
Don’t let the overwhelm overtake you… that’s what cybercriminals want!
Don’t be overwhelmed. IT pros like us already use the most effective tools to prevent cybercrime.
Don’t waste your valuable time searching the internet, reading reviews or guessing at which tools are the best.
